RMAN automatically decrypts backup sets when their contents are restored. In practice, most disk drives have physical block sizes of 512 bytes, so this limitation rarely affects backup to disk drives. For the purposes of a recovery window retention policy, either all of the copies of a backup set are obsolete, or none of them are. To see the effect of these copies under a redundancy-based backup retention policy, use the following command: None of the copies is reported as obsolete because both copies of the backup set have the same values for set_stamp & set_count. Encryption can have a negative effect upon backup performance. The output contains the following: Notice that the set_stamp and set_count values remain the same, but the copy# is incremented for the new backup. Start an RMAN session and then catalog the user-managed mirror copies as datafile copies with the CATALOG command. For the first step, perform the one-time configuration: Then, run the following script at the same time every night to back up the logs generated during the previous day to two separate tape pools: Assume a more sophisticated scenario in which your goal is to back up the archived logs to tape every day. This form of backup is used to back up a database backup created as image copies on disk to tape. Transparently encrypted backups require no intervention to restore, as long as the Oracle Encryption Wallet is open and available. Transparent encryption is best suited for day-to-day backup operations, where backups will be restored at the same database that they were backed up from. For example, enter: The #Copies column shows the number of backupsets, which may have been produced by duplexing or by multiple backup commands. Encryption is performed based on the encryption settings specified with CONFIGURE ENCRYPTION or SET ENCRYPTION. You must have automatic channels configured. To take advantage of the tags associated with your image copy backups, use the WITH TAG selector. This setting applies to all backups except control file autobackups (because the autobackup of a control file always produces one copy) and backup sets when backed up with the BACKUP BACKUPSET command. When restoring a dual-mode encrypted backup, you can use either the Oracle Encryption Wallet or a password for decryption. The DELETE OBSOLETE will purge the backupsets wherever they are and delete all the known copies. With backup optimization, the BACKUP command skips the backup of a file if the identical file has already been backed up to the allocated device type.  In this way, BACKUP BACKUPSET is similar to using the DUPLEX or MAXCOPIES option of BACKUP. To back up backup sets from disk to tape: Assuming that you have configured an automatic sbt channel, issue the BACKUP BACKUPSET command at the RMAN prompt. You decide to back up each copy of the archived redo logs and then delete the originals. For example, you can use the operating system to maintain three identical copies of each file in the database. The following example backs up to an sbt device any archived redo logs that either have not been already backed up, or where the existing backups do not satisfy the current duplexing setting: RMAN does not signal an error when it skips backing up files due to backup optimization. For example, run the following to make three copies of each backup set in the default DISK location: Because you specified COPIES on the BACKUP command, RMAN makes three backupsets of each datafile regardless of the CONFIGURE DATAFILE COPIES setting. The V$RMAN_ENCRYPTION_ALGORITHMS view contains a list of encryption algorithms supported by RMAN.
In this way, BACKUP BACKUPSET is similar to using the DUPLEX or MAXCOPIES option of BACKUP. To back up backup sets from disk to tape: Assuming that you have configured an automatic sbt channel, issue the BACKUP BACKUPSET command at the RMAN prompt. You decide to back up each copy of the archived redo logs and then delete the originals. For example, you can use the operating system to maintain three identical copies of each file in the database. The following example backs up to an sbt device any archived redo logs that either have not been already backed up, or where the existing backups do not satisfy the current duplexing setting: RMAN does not signal an error when it skips backing up files due to backup optimization. For example, run the following to make three copies of each backup set in the default DISK location: Because you specified COPIES on the BACKUP command, RMAN makes three backupsets of each datafile regardless of the CONFIGURE DATAFILE COPIES setting. The V$RMAN_ENCRYPTION_ALGORITHMS view contains a list of encryption algorithms supported by RMAN.  This chapter contains these topics: Configuring and Allocating Channels for Use in Backups, Backing Up Existing Image Copy Backups with RMAN. If you use the LIST BACKUPS command, the output contains the list of all copies (including copies created by BACKUP BACKUPSET command). Encryption is configured for backups of the whole database or at least one tablespace. For example, enter: You could also use ALTER DATABASE END BACKUP to take all tablespaces out of backup mode. You can use the CHANNEL parameter so that RMAN writes all backup sets for a backupSpec to a specific channel. After a corrupt block is repaired, the row identifying this block is deleted from the view. To see the effect of these copies under a redundancy-based backup retention policy, use the following command: None of the copies is reported as obsolete because both copies of the backup set have the same same values for set_stamp & set_count. For the purposes of a redundancy-based backup retention policy, a backup set is counted as one instance of backup, even if there are multiple copies of the backup pieces that make up backup set, such as when a backup set has been backed up from disk to tape. You can override this behavior and include the example tablespace as follows: Assume that you back up the database and archived logs every night to tape by running this command: The preceding command sets an upper limit to the size of each backup set so that RMAN produces multiple backup sets. But it does not require to recatalog the backup files as RMAN is doing this automatically. Specify the number of identical copies with the COPIES option of the BACKUP command. In which schema do temporary tables go in PostgreSQL. RMAN can make up to four copies of a backup set simultaneously, each an exact duplicate of the others. You do not have to specify a SKIP clause on the BACKUP command. (Note that the degree of backup duplexing configured or specified in the BACKUP command determines the number of output files, independent of the number of input files. This example keeps the backup of the database indefinitely and does not save archived logs needed to recover it: Run the CONFIGURE BACKUP OPTIMIZATION command to enable backup optimization. And RMAN catalog is up-to-date. RMAN does not automate the splitting of mirrors, but can make use of split mirrors in backup and recovery operations. Encrypted backups cannot be read if they are obtained by unauthorized people. The SUSPEND/RESUME feature is not required for split mirror backups in most cases, although it is necessary if your system requires the database cache to be free of dirty buffers before the volume can be split. Which algorithm to use for encrypting backups. There is no persistent configuration that controls whether archivelog backups as backupsets are encrypted. If you wish to modify your existing backup environment so that all RMAN backups are encrypted, perform the following steps: After these steps, all RMAN backup sets created by this database will be encrypted, unless you explicitly override this behavior for an RMAN session with: This remains in effect until you issue the SET ENCRYPTION OFF command during an RMAN session, or change the persistent setting again with: The BACKUP command arguments do not change for creating encrypted backups.
This chapter contains these topics: Configuring and Allocating Channels for Use in Backups, Backing Up Existing Image Copy Backups with RMAN. If you use the LIST BACKUPS command, the output contains the list of all copies (including copies created by BACKUP BACKUPSET command). Encryption is configured for backups of the whole database or at least one tablespace. For example, enter: You could also use ALTER DATABASE END BACKUP to take all tablespaces out of backup mode. You can use the CHANNEL parameter so that RMAN writes all backup sets for a backupSpec to a specific channel. After a corrupt block is repaired, the row identifying this block is deleted from the view. To see the effect of these copies under a redundancy-based backup retention policy, use the following command: None of the copies is reported as obsolete because both copies of the backup set have the same same values for set_stamp & set_count. For the purposes of a redundancy-based backup retention policy, a backup set is counted as one instance of backup, even if there are multiple copies of the backup pieces that make up backup set, such as when a backup set has been backed up from disk to tape. You can override this behavior and include the example tablespace as follows: Assume that you back up the database and archived logs every night to tape by running this command: The preceding command sets an upper limit to the size of each backup set so that RMAN produces multiple backup sets. But it does not require to recatalog the backup files as RMAN is doing this automatically. Specify the number of identical copies with the COPIES option of the BACKUP command. In which schema do temporary tables go in PostgreSQL. RMAN can make up to four copies of a backup set simultaneously, each an exact duplicate of the others. You do not have to specify a SKIP clause on the BACKUP command. (Note that the degree of backup duplexing configured or specified in the BACKUP command determines the number of output files, independent of the number of input files. This example keeps the backup of the database indefinitely and does not save archived logs needed to recover it: Run the CONFIGURE BACKUP OPTIMIZATION command to enable backup optimization. And RMAN catalog is up-to-date. RMAN does not automate the splitting of mirrors, but can make use of split mirrors in backup and recovery operations. Encrypted backups cannot be read if they are obtained by unauthorized people. The SUSPEND/RESUME feature is not required for split mirror backups in most cases, although it is necessary if your system requires the database cache to be free of dirty buffers before the volume can be split. Which algorithm to use for encrypting backups. There is no persistent configuration that controls whether archivelog backups as backupsets are encrypted. If you wish to modify your existing backup environment so that all RMAN backups are encrypted, perform the following steps: After these steps, all RMAN backup sets created by this database will be encrypted, unless you explicitly override this behavior for an RMAN session with: This remains in effect until you issue the SET ENCRYPTION OFF command during an RMAN session, or change the persistent setting again with: The BACKUP command arguments do not change for creating encrypted backups.
This is easier to understand if you look at the output of the LIST and REPORT commands. The script performs a shutdown, startup, shutdown, and then startup again before creating multiple copies of the backup: Note the inclusion of the current control file with the backup, and the use of the tag to identify the backup. You can do that with a BACKUP BACKUPSET COMPLETED AFTER and no DELETE INPUT for basically the same as a cp or copy command: Thats it, you now have a first destination for newest backups, and a second one for all the backups. Finally, you delete old logs. In this case, allocate one DISK channel for each disk drive and specify the format string on the ALLOCATE CHANNEL command so that the filenames are on different disks. This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces. For example, RMAN may show output similar to the following: You cannot use the MAXCORRUPT or PROXY parameters with the VALIDATE option. With the restartable backup feature, RMAN backs up only those files that were not backed up after a specified date. For improved security, RMAN backups created as backup sets can be encrypted. You can use the MAXSETSIZE parameter of the BACKUP command to set a maximum size for each backup set. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. First of all, take a backup on the first destination: This is a small database and backup is done with the default single channel, so there is only two backupsets, one for the datafiles and the other for the controlfile and the spfile: Its quite easy to move the backup to the long term destination with RMAN: BACKUP BACKUPSET with DELETE INPUT is basically the same as a system mv or move. When using transparent encryption, you must first configure the Oracle Encryption Wallet, as described in the documentation for Oracle's Transparent Data Encryption feature. Nous sommes des experts des infrastructures et plateformes de donnes innovantes et efficientes. You can think about tapes or you can connect RMAN to a global backup tool, but it requires additional libraries that are not free, and it definitely adds complexity. Hence, it can remove all logs from both ?/oradata/trgt/arch/dest_1 and ?/oradata/trgt/arch/dest_2. dbi services est une entreprise spcialise dans le consulting et les services IT. A copy of a backup set is a copy of each backup piece in the backup set, with each copy getting a unique copy number (for example, 0tcm8u2s_1_1 and 0tcm8u2s_1_2). Use the MAXSETSIZE parameter to override this calculation and specify how many files should go in each backup set. For example, perform the following backup: Now, run the LIST command. If a datafile has more corrupt blocks than specified by the MAXCORRUPT parameter, the command terminates. You can use the VALIDATE keyword of the BACKUP command to do the following: Check datafiles for physical and logical corruption, Confirm that all database files exist and are in the correct locations. You want to back up only those archived redo logs required to recover this online backup.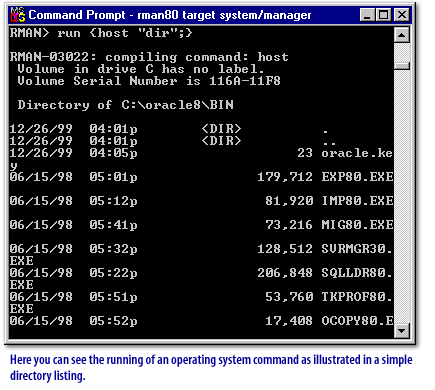 The new backup will be tagged with the same tag as the image copy backup being backed up. Take the database out of the suspended state: Take the tablespaces out of backup mode. The easiest solution in this case is to use the DELETE ALL INPUT option means that RMAN deletes all logs that match the ARCHIVELOG criteria. For example, to always limit the backup piece size to 2GB or less, you can configure the automatic DISK channel as follows and then run BACKUP DATABASE: Note that in version 2.0 of the media management API, media management vendors can specify the maximum size of a backup piece that can be written to their media manager. Set a password for backup encryption, persisting until the RMAN client exits. Adding INCLUDE CURRENT CONTROLFILE ensures that a usable backup of the control file is included with the backup and tagged in order to simplify restoring the control file with the rest of the database. To use password encryption, use the SET ENCRYPTION ON IDENTIFIED BY password ONLY command in your RMAN scripts. Note that it is not possible to duplex backup sets to the flash recovery area, and that duplexing only applies to backup sets, not image copies. The other method is to allocate channels manually within a RUN block before running the BACKUP command. See "Restartable Backups" for a conceptual overview of restartable backups. Override the encryption settings specified by the CONFIGURE ENCRYPTION command. Assume that the media management device fails halfway through the backup and is then restarted. For example, issue: You can distribute backups in this manner by default in the future, by configuring channels as follows: If you specify a nonexistent directory, RMAN displays output such as the following: When making backups, RMAN divides the total number of files requiring backups by the number of allocated channels to calculate the number of files to place in each backup set. For the purposes of a recovery window retention policy, either all of the copies of a backup set are obsolete, or none of them are. For example, enter: Many sites keep an backup of the database stored on disk in case a failure occurs on the primary database or an incorrect user action such as a DROP TABLE requires point-in-time recovery. Like a mv command you can put again your backup in previous destination: All the backupsets are now back to the first destination only, and you can see another increase on the filename. You can specify parameters to prevent termination, as listed in the following table. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. Issue a LIST BACKUP command to see a listing of backup sets and pieces (the #Copies column shows the number of copies, which may have been produced through duplexing or through multiple invocations of the BACKUP command). This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces.
The new backup will be tagged with the same tag as the image copy backup being backed up. Take the database out of the suspended state: Take the tablespaces out of backup mode. The easiest solution in this case is to use the DELETE ALL INPUT option means that RMAN deletes all logs that match the ARCHIVELOG criteria. For example, to always limit the backup piece size to 2GB or less, you can configure the automatic DISK channel as follows and then run BACKUP DATABASE: Note that in version 2.0 of the media management API, media management vendors can specify the maximum size of a backup piece that can be written to their media manager. Set a password for backup encryption, persisting until the RMAN client exits. Adding INCLUDE CURRENT CONTROLFILE ensures that a usable backup of the control file is included with the backup and tagged in order to simplify restoring the control file with the rest of the database. To use password encryption, use the SET ENCRYPTION ON IDENTIFIED BY password ONLY command in your RMAN scripts. Note that it is not possible to duplex backup sets to the flash recovery area, and that duplexing only applies to backup sets, not image copies. The other method is to allocate channels manually within a RUN block before running the BACKUP command. See "Restartable Backups" for a conceptual overview of restartable backups. Override the encryption settings specified by the CONFIGURE ENCRYPTION command. Assume that the media management device fails halfway through the backup and is then restarted. For example, issue: You can distribute backups in this manner by default in the future, by configuring channels as follows: If you specify a nonexistent directory, RMAN displays output such as the following: When making backups, RMAN divides the total number of files requiring backups by the number of allocated channels to calculate the number of files to place in each backup set. For the purposes of a recovery window retention policy, either all of the copies of a backup set are obsolete, or none of them are. For example, enter: Many sites keep an backup of the database stored on disk in case a failure occurs on the primary database or an incorrect user action such as a DROP TABLE requires point-in-time recovery. Like a mv command you can put again your backup in previous destination: All the backupsets are now back to the first destination only, and you can see another increase on the filename. You can specify parameters to prevent termination, as listed in the following table. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. Issue a LIST BACKUP command to see a listing of backup sets and pieces (the #Copies column shows the number of copies, which may have been produced through duplexing or through multiple invocations of the BACKUP command). This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces.
 In this way, BACKUP BACKUPSET is similar to using the DUPLEX or MAXCOPIES option of BACKUP. To back up backup sets from disk to tape: Assuming that you have configured an automatic sbt channel, issue the BACKUP BACKUPSET command at the RMAN prompt. You decide to back up each copy of the archived redo logs and then delete the originals. For example, you can use the operating system to maintain three identical copies of each file in the database. The following example backs up to an sbt device any archived redo logs that either have not been already backed up, or where the existing backups do not satisfy the current duplexing setting: RMAN does not signal an error when it skips backing up files due to backup optimization. For example, run the following to make three copies of each backup set in the default DISK location: Because you specified COPIES on the BACKUP command, RMAN makes three backupsets of each datafile regardless of the CONFIGURE DATAFILE COPIES setting. The V$RMAN_ENCRYPTION_ALGORITHMS view contains a list of encryption algorithms supported by RMAN.
In this way, BACKUP BACKUPSET is similar to using the DUPLEX or MAXCOPIES option of BACKUP. To back up backup sets from disk to tape: Assuming that you have configured an automatic sbt channel, issue the BACKUP BACKUPSET command at the RMAN prompt. You decide to back up each copy of the archived redo logs and then delete the originals. For example, you can use the operating system to maintain three identical copies of each file in the database. The following example backs up to an sbt device any archived redo logs that either have not been already backed up, or where the existing backups do not satisfy the current duplexing setting: RMAN does not signal an error when it skips backing up files due to backup optimization. For example, run the following to make three copies of each backup set in the default DISK location: Because you specified COPIES on the BACKUP command, RMAN makes three backupsets of each datafile regardless of the CONFIGURE DATAFILE COPIES setting. The V$RMAN_ENCRYPTION_ALGORITHMS view contains a list of encryption algorithms supported by RMAN.  This chapter contains these topics: Configuring and Allocating Channels for Use in Backups, Backing Up Existing Image Copy Backups with RMAN. If you use the LIST BACKUPS command, the output contains the list of all copies (including copies created by BACKUP BACKUPSET command). Encryption is configured for backups of the whole database or at least one tablespace. For example, enter: You could also use ALTER DATABASE END BACKUP to take all tablespaces out of backup mode. You can use the CHANNEL parameter so that RMAN writes all backup sets for a backupSpec to a specific channel. After a corrupt block is repaired, the row identifying this block is deleted from the view. To see the effect of these copies under a redundancy-based backup retention policy, use the following command: None of the copies is reported as obsolete because both copies of the backup set have the same same values for set_stamp & set_count. For the purposes of a redundancy-based backup retention policy, a backup set is counted as one instance of backup, even if there are multiple copies of the backup pieces that make up backup set, such as when a backup set has been backed up from disk to tape. You can override this behavior and include the example tablespace as follows: Assume that you back up the database and archived logs every night to tape by running this command: The preceding command sets an upper limit to the size of each backup set so that RMAN produces multiple backup sets. But it does not require to recatalog the backup files as RMAN is doing this automatically. Specify the number of identical copies with the COPIES option of the BACKUP command. In which schema do temporary tables go in PostgreSQL. RMAN can make up to four copies of a backup set simultaneously, each an exact duplicate of the others. You do not have to specify a SKIP clause on the BACKUP command. (Note that the degree of backup duplexing configured or specified in the BACKUP command determines the number of output files, independent of the number of input files. This example keeps the backup of the database indefinitely and does not save archived logs needed to recover it: Run the CONFIGURE BACKUP OPTIMIZATION command to enable backup optimization. And RMAN catalog is up-to-date. RMAN does not automate the splitting of mirrors, but can make use of split mirrors in backup and recovery operations. Encrypted backups cannot be read if they are obtained by unauthorized people. The SUSPEND/RESUME feature is not required for split mirror backups in most cases, although it is necessary if your system requires the database cache to be free of dirty buffers before the volume can be split. Which algorithm to use for encrypting backups. There is no persistent configuration that controls whether archivelog backups as backupsets are encrypted. If you wish to modify your existing backup environment so that all RMAN backups are encrypted, perform the following steps: After these steps, all RMAN backup sets created by this database will be encrypted, unless you explicitly override this behavior for an RMAN session with: This remains in effect until you issue the SET ENCRYPTION OFF command during an RMAN session, or change the persistent setting again with: The BACKUP command arguments do not change for creating encrypted backups.
This chapter contains these topics: Configuring and Allocating Channels for Use in Backups, Backing Up Existing Image Copy Backups with RMAN. If you use the LIST BACKUPS command, the output contains the list of all copies (including copies created by BACKUP BACKUPSET command). Encryption is configured for backups of the whole database or at least one tablespace. For example, enter: You could also use ALTER DATABASE END BACKUP to take all tablespaces out of backup mode. You can use the CHANNEL parameter so that RMAN writes all backup sets for a backupSpec to a specific channel. After a corrupt block is repaired, the row identifying this block is deleted from the view. To see the effect of these copies under a redundancy-based backup retention policy, use the following command: None of the copies is reported as obsolete because both copies of the backup set have the same same values for set_stamp & set_count. For the purposes of a redundancy-based backup retention policy, a backup set is counted as one instance of backup, even if there are multiple copies of the backup pieces that make up backup set, such as when a backup set has been backed up from disk to tape. You can override this behavior and include the example tablespace as follows: Assume that you back up the database and archived logs every night to tape by running this command: The preceding command sets an upper limit to the size of each backup set so that RMAN produces multiple backup sets. But it does not require to recatalog the backup files as RMAN is doing this automatically. Specify the number of identical copies with the COPIES option of the BACKUP command. In which schema do temporary tables go in PostgreSQL. RMAN can make up to four copies of a backup set simultaneously, each an exact duplicate of the others. You do not have to specify a SKIP clause on the BACKUP command. (Note that the degree of backup duplexing configured or specified in the BACKUP command determines the number of output files, independent of the number of input files. This example keeps the backup of the database indefinitely and does not save archived logs needed to recover it: Run the CONFIGURE BACKUP OPTIMIZATION command to enable backup optimization. And RMAN catalog is up-to-date. RMAN does not automate the splitting of mirrors, but can make use of split mirrors in backup and recovery operations. Encrypted backups cannot be read if they are obtained by unauthorized people. The SUSPEND/RESUME feature is not required for split mirror backups in most cases, although it is necessary if your system requires the database cache to be free of dirty buffers before the volume can be split. Which algorithm to use for encrypting backups. There is no persistent configuration that controls whether archivelog backups as backupsets are encrypted. If you wish to modify your existing backup environment so that all RMAN backups are encrypted, perform the following steps: After these steps, all RMAN backup sets created by this database will be encrypted, unless you explicitly override this behavior for an RMAN session with: This remains in effect until you issue the SET ENCRYPTION OFF command during an RMAN session, or change the persistent setting again with: The BACKUP command arguments do not change for creating encrypted backups. This is easier to understand if you look at the output of the LIST and REPORT commands. The script performs a shutdown, startup, shutdown, and then startup again before creating multiple copies of the backup: Note the inclusion of the current control file with the backup, and the use of the tag to identify the backup. You can do that with a BACKUP BACKUPSET COMPLETED AFTER and no DELETE INPUT for basically the same as a cp or copy command: Thats it, you now have a first destination for newest backups, and a second one for all the backups. Finally, you delete old logs. In this case, allocate one DISK channel for each disk drive and specify the format string on the ALLOCATE CHANNEL command so that the filenames are on different disks. This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces. For example, RMAN may show output similar to the following: You cannot use the MAXCORRUPT or PROXY parameters with the VALIDATE option. With the restartable backup feature, RMAN backs up only those files that were not backed up after a specified date. For improved security, RMAN backups created as backup sets can be encrypted. You can use the MAXSETSIZE parameter of the BACKUP command to set a maximum size for each backup set. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. First of all, take a backup on the first destination: This is a small database and backup is done with the default single channel, so there is only two backupsets, one for the datafiles and the other for the controlfile and the spfile: Its quite easy to move the backup to the long term destination with RMAN: BACKUP BACKUPSET with DELETE INPUT is basically the same as a system mv or move. When using transparent encryption, you must first configure the Oracle Encryption Wallet, as described in the documentation for Oracle's Transparent Data Encryption feature. Nous sommes des experts des infrastructures et plateformes de donnes innovantes et efficientes. You can think about tapes or you can connect RMAN to a global backup tool, but it requires additional libraries that are not free, and it definitely adds complexity. Hence, it can remove all logs from both ?/oradata/trgt/arch/dest_1 and ?/oradata/trgt/arch/dest_2. dbi services est une entreprise spcialise dans le consulting et les services IT. A copy of a backup set is a copy of each backup piece in the backup set, with each copy getting a unique copy number (for example, 0tcm8u2s_1_1 and 0tcm8u2s_1_2). Use the MAXSETSIZE parameter to override this calculation and specify how many files should go in each backup set. For example, perform the following backup: Now, run the LIST command. If a datafile has more corrupt blocks than specified by the MAXCORRUPT parameter, the command terminates. You can use the VALIDATE keyword of the BACKUP command to do the following: Check datafiles for physical and logical corruption, Confirm that all database files exist and are in the correct locations. You want to back up only those archived redo logs required to recover this online backup.
 The new backup will be tagged with the same tag as the image copy backup being backed up. Take the database out of the suspended state: Take the tablespaces out of backup mode. The easiest solution in this case is to use the DELETE ALL INPUT option means that RMAN deletes all logs that match the ARCHIVELOG criteria. For example, to always limit the backup piece size to 2GB or less, you can configure the automatic DISK channel as follows and then run BACKUP DATABASE: Note that in version 2.0 of the media management API, media management vendors can specify the maximum size of a backup piece that can be written to their media manager. Set a password for backup encryption, persisting until the RMAN client exits. Adding INCLUDE CURRENT CONTROLFILE ensures that a usable backup of the control file is included with the backup and tagged in order to simplify restoring the control file with the rest of the database. To use password encryption, use the SET ENCRYPTION ON IDENTIFIED BY password ONLY command in your RMAN scripts. Note that it is not possible to duplex backup sets to the flash recovery area, and that duplexing only applies to backup sets, not image copies. The other method is to allocate channels manually within a RUN block before running the BACKUP command. See "Restartable Backups" for a conceptual overview of restartable backups. Override the encryption settings specified by the CONFIGURE ENCRYPTION command. Assume that the media management device fails halfway through the backup and is then restarted. For example, issue: You can distribute backups in this manner by default in the future, by configuring channels as follows: If you specify a nonexistent directory, RMAN displays output such as the following: When making backups, RMAN divides the total number of files requiring backups by the number of allocated channels to calculate the number of files to place in each backup set. For the purposes of a recovery window retention policy, either all of the copies of a backup set are obsolete, or none of them are. For example, enter: Many sites keep an backup of the database stored on disk in case a failure occurs on the primary database or an incorrect user action such as a DROP TABLE requires point-in-time recovery. Like a mv command you can put again your backup in previous destination: All the backupsets are now back to the first destination only, and you can see another increase on the filename. You can specify parameters to prevent termination, as listed in the following table. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. Issue a LIST BACKUP command to see a listing of backup sets and pieces (the #Copies column shows the number of copies, which may have been produced through duplexing or through multiple invocations of the BACKUP command). This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces.
The new backup will be tagged with the same tag as the image copy backup being backed up. Take the database out of the suspended state: Take the tablespaces out of backup mode. The easiest solution in this case is to use the DELETE ALL INPUT option means that RMAN deletes all logs that match the ARCHIVELOG criteria. For example, to always limit the backup piece size to 2GB or less, you can configure the automatic DISK channel as follows and then run BACKUP DATABASE: Note that in version 2.0 of the media management API, media management vendors can specify the maximum size of a backup piece that can be written to their media manager. Set a password for backup encryption, persisting until the RMAN client exits. Adding INCLUDE CURRENT CONTROLFILE ensures that a usable backup of the control file is included with the backup and tagged in order to simplify restoring the control file with the rest of the database. To use password encryption, use the SET ENCRYPTION ON IDENTIFIED BY password ONLY command in your RMAN scripts. Note that it is not possible to duplex backup sets to the flash recovery area, and that duplexing only applies to backup sets, not image copies. The other method is to allocate channels manually within a RUN block before running the BACKUP command. See "Restartable Backups" for a conceptual overview of restartable backups. Override the encryption settings specified by the CONFIGURE ENCRYPTION command. Assume that the media management device fails halfway through the backup and is then restarted. For example, issue: You can distribute backups in this manner by default in the future, by configuring channels as follows: If you specify a nonexistent directory, RMAN displays output such as the following: When making backups, RMAN divides the total number of files requiring backups by the number of allocated channels to calculate the number of files to place in each backup set. For the purposes of a recovery window retention policy, either all of the copies of a backup set are obsolete, or none of them are. For example, enter: Many sites keep an backup of the database stored on disk in case a failure occurs on the primary database or an incorrect user action such as a DROP TABLE requires point-in-time recovery. Like a mv command you can put again your backup in previous destination: All the backupsets are now back to the first destination only, and you can see another increase on the filename. You can specify parameters to prevent termination, as listed in the following table. The extra copy of a backup set created by BACKUP BACKUPSET is not considered to be a new backup set, as the several copies of a backup set produced by these other forms of the BACKUP command are not separate backup sets. Issue a LIST BACKUP command to see a listing of backup sets and pieces (the #Copies column shows the number of copies, which may have been produced through duplexing or through multiple invocations of the BACKUP command). This example backs up all disk backup sets to tape: This example backs up all disk backup sets to tape and then deletes the input disk backups: Issue a LIST command to see a listing of backup sets and pieces.