It organizes the. What are the drawbacks of employing the shadow-paging technique? M.sc[CS&IT] Database Shadowing is a backup strategy whereby a full copy of the users database is maintained at an alternate information processing facility. Hard to extend algorithm to allow transaction to run concurrently. 0000017072 00000 n
A:This question is related to protocols. It fills, A:Backpatching can be defined as the process of resolving forward branches that are inside the code.. A:This fill in the blank question is related to networks. Q:NAT is known as ________________ translation. Draw the framework of error detection mechanism, A:According to the information given:- A Pigpen cipher encrypts, Q:How many error detection mechanisms do you know? Specifically address the type of, A:Huffman Coding: In the shadow-copy scheme, a transaction that wants to update the database first creates a complete copy of the database. The ciphertext generated, Q:None 101 23
Q:The . AI and Machine Learning Demystified by Carol Smith at Midwest UX 2017, Pew Research Center's Internet & American Life Project, Harry Surden - Artificial Intelligence and Law Overview, Pinot: Realtime Distributed OLAP datastore, How to Become a Thought Leader in Your Niche, UX, ethnography and possibilities: for Libraries, Museums and Archives, Winners and Losers - All the (Russian) President's Men, No public clipboards found for this slide, Now What? Chapter 3 memory management, recent systems, Unix Memory Management - Operating Systems, Database concurrency control & recovery (1), NETWORK DEVICE SECURITY NETWORK HARDENING, DIGITAL VIDEO DATA SIZING AND OBJECT BASED ANIMATION, Mining single dimensional boolean association rules from transactional, pointer, virtual function and polymorphism, Managing console i/o operation,working with files, microcomputer architecture - Arithmetic instruction, Be A Great Product Leader (Amplify, Oct 2019), Trillion Dollar Coach Book (Bill Campbell). 0000007818 00000 n
The method, A:For regression, We know that the equation of a line is given by y=mx+b, wheremis the slope andb. Q:What is The Extended form of SHDSL in computers? Hardware failures may include memory errors, disk crashes, bad disk sectors, and disk full of errors among others.
0000016802 00000 n 123 0 obj<>stream SlideShare uses cookies to improve functionality and performance, and to provide you with relevant advertising. Under what circumstances does shadow paging not require a log? *Response times may vary by subject and question complexity. It does not require the use of log in a single user environment. Find answers to questions asked by students like you. What are the advantages of Aries in DBMS? Shadow Paging maintains 2 page table. 0000015207 00000 n We all know that recovery means to get back the information, which is lost. <]>> After every transaction completion database pages containing old version of modified data need to be garbage collected. Page table is an index of pages. Looks like youve clipped this slide to already. Under certain circumstances, shadow paging may require fewer disk accesses than do the log-based methods discussed previously. For the source coding:What is/are the benefit(s) of calculating entropy? 0000017125 00000 n Activate your 30 day free trialto continue reading. Instant access to millions of ebooks, audiobooks, magazines, podcasts and more. P = C E (IV +n, K) 101 0 obj <> endobj The old copy of the database has not been affected. trailer 0 Affine cipher is not susceptible to frequency analysis. Send Flowers internationally on the Same Day, Solar System For Cannabis Indoor Farming House: Saving Your Bill, Best Affiliate Programs To Make Money In 2021. What are the advantages and disadvantages of the MUX and the decoder methods over one another? What are the differences between Huffman coding and LZW coding? xb```"wV| &{9-N. A:Solution:-- Shadow Database is an optional software facility available with Reality, whereby two copies of a database are maintained on the same system to enhance the resilience of the database in the event of a failure. 0000001737 00000 n Lookup table: A:In given question we have asked what is the probability that a bit string of length 8 has exactly, A:Backpatching It helps to maintain database consistency in case of failure. A:Given question is related to protocols in computer science. Initially we are provided with a string of characters known as plain text and a number know. Blockchain + AI + Crypto Economics Are We Creating a Code Tsunami? If you continue browsing the site, you agree to the use of cookies on this website. 0000009846 00000 n 0000001658 00000 n A:This question requires short form of given term. No change in the satisfaction ability of the Skolem standard form is achieved by the. It helps to maintain database consistency in case of failure.Advantages. What are the disadvantages of using the shadow-paging technique? See our Privacy Policy and User Agreement for details. What is/are the benefit(s) of calculating entropy? The compressed sparse row (CSR) or Yale format is a similar array, Q:Describe the key design ideas of Block cipher, A:The Feistel cypher structure is used in the construction of block cyphers. 0000011606 00000 n A:In artificial intelligence, the given message is encoded into a coded form; hence, it is not, Q:What is the relative efficiency of RCBD (Randomized Completely Block Design) over CRD (Completely, A:The relative efficiency of RCBD (Randomized Completely Block Design) over CRD (Completely Randomized, Q:If we use 12-bit pixel values in a lookup table representation, how many entries does Q:Affine cipher is not susceptible to frequency analysis. We use cookies to ensure that we give you the best experience on our website. Paging is a sort of memory storage that, Q:If you use 2-byte pixel values in a 24-bit lookup table representation, how many bytes does the, A:Definition: 0000000016 00000 n Aries supports page-level and record-level locking in a uniform fashion. False. A:Required:
* Block size of 128 bits Q:What is The Full form of VOIP in Computer Science? layer of OSI model can use the trailer of the frame for error detection. Median response time is 34 minutes for paid subscribers and may be longer for promotional offers. Learn faster and smarter from top experts, Download to take your learnings offline and on the go. For AES with a 128-bit block length and a 128-bit key length, what is the output, Q:Write the necessary steps for AES to do encryption and decryption with well-arranged diagrams for, A:According to the question we need to write the necessary steps for AES to do encryption and, A:Systematic error detection: A disadvantage of the general monoalphabetic cipher is that both sender and Q:3. startxref The advantages of paging must be determined. Structured English uses a simple English language to make structured programming easier for non-professionals.
Shadow paging is a copy-on-write technique for avoiding in-place updates of pages. For example, it is hard to extend shadow paging to allow multiple transactions to execute concurrently. We all know that recovery means to get back the information, which is lost. Give suitable reason for the solution, For AES with a 128 bit block length and a 128-bit key length, what is the output of the first round of AES if the plaintext consists of 128 1's and the first subkey also consists of 128 zeroes. A shadow database is a database that is built and used inside organizations, without IT knowledge or approval (hence the shadow in the title). The SlideShare family just got bigger. A:Answer 3 a) its named after lord playfair. BUFFER MANAGEMENT A:The answer for given question is option (C) Q# Pigpen cipher is not susceptible to frequency analysis.
So, the answer is, A MUX is a, Q:(True/False): Linking OBJ modules is much faster than assembling ASM source files, A:The time taken to assemble large source files will be more and because of it the code is being, A:Introduction:
0000001769 00000 n 0000001333 00000 n Does the Hamming code have a pattern? First of all, we have to understand what multiplexer is?? 16VE. Lookup table: 0000013375 00000 n In a computer operating system, paging is used for faster access of the data. The program is divided into various parts that are known as logical statements. Answer is in, A:Introduction of Paging: 0000003917 00000 n Therefore, data is transformed into, A:- The question wants to validate the statement that data is transferred into key-value pairs when, A:The question is on: The statement "MapReduce works on key-value pairs for input and output., Q:implements the Frame Check Sequence (FCS) using a technique called Cylic Redundancy Check (CRC).True, A:Required: We have to explain error detection mechanisms and framework of, Q:For CTR, on the lecture notes, it shows the decryption rule is Start your trial now! Q:What is The Compressed form of Multivariant Curve Resolution in Computers? %%EOF Which of the following are disadvantages of shadow paging? Q:Can someone explain to me what the trace back error means? True A:Answer is Data Link Layer The current page table may be kept in main memory (volatile storage). Enjoy access to millions of ebooks, audiobooks, magazines, and more from Scribd. Shadow paging is one of the techniques that is used to recover from failure. Flexible buffer management during restart and normal processing. Q:What is The Full form of XMPP in Computer Science? Q:What is The Full form of MIPS in Computer Science? 0000017207 00000 n The lookup table is mainly an array which will replace the. What are the disadvantages of shadow paging recovery technique? 0000016733 00000 n SHADOW PAGING AND Recovery not affected by granularity of locking. 3. OF ARTS & SCIENCE , NADAR SARASWATHI COLLEGE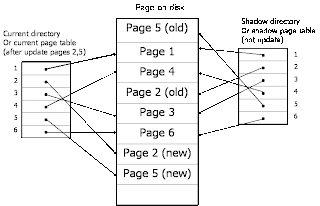 0000000756 00000 n
Describe its principle of operation, A:Fingerprints are made of an arrangement of ridges called friction ridges. However, a multiuser environment requires log for concurrency control. Q:What is the full form of VoIP in Computer Science? If you continue to use this site we will assume that you are happy with it. Due to location change on disk due to update database it is quite difficult to keep related pages in database closer on disk. %PDF-1.4
%
Python implementation. PRESENTED BY Disadvantages: Data gets fragmented or scattered. VADAPUDUPATTI , THENI.
0000000756 00000 n
Describe its principle of operation, A:Fingerprints are made of an arrangement of ridges called friction ridges. However, a multiuser environment requires log for concurrency control. Q:What is the full form of VoIP in Computer Science? If you continue to use this site we will assume that you are happy with it. Due to location change on disk due to update database it is quite difficult to keep related pages in database closer on disk. %PDF-1.4
%
Python implementation. PRESENTED BY Disadvantages: Data gets fragmented or scattered. VADAPUDUPATTI , THENI.
A:What are the difference between semaphores and mutexes? Explain, True/False In computer science, shadow paging is a technique for providing atomicity and durability (two of the ACID properties) in database systems. During commit operation, changed blocks are going to be pointed by shadow page table which have to be returned to collection of free blocks otherwise they become accessible. T or F, A:Pigpen cipher: but, for the main function in the. Step 1 Page is a segment of memory. First week only $4.99. * Flexibility of, Q:For AES with a 128 bit block length and a 128-bit key length, what is the output of the first round, A:Given requirement, In each ridge, there are, A:Introduction: These databases are usually created by individual employees using Excel spreadsheets, notes on their desktop using Word, or Outlook contact, etc. 0000001416 00000 n This scheme is based on making copies of the database, called shadow copies, assumes that only one transaction is active at a time. Is Ea typo?, A:No, its not a typo as a many algorithm uses the E meaning encryption to decrypt the real meaning of. 0000017263 00000 n If you continue browsing the site, you agree to the use of cookies on this website. : How to Move Forward When We're Divided (About Basically Everything), Already Enough: A Path to Self-Acceptance, Full Out: Lessons in Life and Leadership from America's Favorite Coach, How to Be Perfect: The Correct Answer to Every Moral Question, Uninvited: Living Loved When You Feel Less Than, Left Out, and Lonely, Girl, Wash Your Face: Stop Believing the Lies About Who You Are so You Can Become Who You Were Meant to Be, Boundaries Updated and Expanded Edition: When to Say Yes, How to Say No To Take Control of Your Life, Never Split the Difference: Negotiating As If Your Life Depended On It, The 7 Habits of Highly Effective People Personal Workbook, Less Fret, More Faith: An 11-Week Action Plan to Overcome Anxiety, Girl, Stop Apologizing: A Shame-Free Plan for Embracing and Achieving Your Goals, The 7 Habits of Highly Effective People: Powerful Lessons in Personal Change: 25th Anniversary Infographics Edition, Anxious for Nothing: Finding Calm in a Chaotic World, Plays Well with Others: The Surprising Science Behind Why Everything You Know About Relationships is (Mostly) Wrong, Ahead of the Curve: Using Consumer Psychology to Meet Your Business Goals, Be the Love: Seven Ways to Unlock Your Heart and Manifest Happiness, Momentum: Setting Goals with Clarity, Intention, and Action, Do Hard Things: Why We Get Resilience Wrong and the Surprising Science of Real Toughness, How to Transform a Broken Heart: A Survival Guide for Breakups, Complicated Relationships, and Other Losses, Golden: The Power of Silence in a World of Noise, Stimulus Wreck: Rebuilding After a Financial Disaster, Endure: How to Work Hard, Outlast, and Keep Hammering, Courage and Crucibles: Leadership in Challenging Times, Speak: Find Your Voice, Trust Your Gut, and Get From Where You Are to Where You Want To Be, Life Lessons Harry Potter Taught Me: Discover the Magic of Friendship, Family, Courage, and Love in Your Life, The Expectation Effect: How Your Mindset Can Change Your World, The Mom Friend Guide to Everyday Safety and Security: Tips from the Practical One in Your Squad, Dad on Pills: Fatherhood and Mental Illness. A:In digital signal processing and related fields, sampling and quantization are two methods, rather. A`BC + AB`C` +AB, Data And Network Communication Technology. Systematic error detection is a technique where the error-checking, Q:Explain how to break a character substitution cipher, A:Answer: One copy is enabled as the live database to which users can log on. Specifically address the type of redundancy addressed by each method. Huffman encoding is an algorithm that encodes data in a lossless manner. In computer science, Algorithms for Recovery and Isolation Exploiting Semantics, or ARIES is a recovery algorithm designed to work with a no-force, steal database approach; it is used by IBM DB2, Microsoft SQL Server and many other database systems. A:Compressed sparse row: Q:MapReduce works on key-value pairs for input and output. Ethernet implements the Frame Check Sequence (FCS) using a technique called Cylic. Shadow Paging is a recovery technique that provides atomicity and durablity in database system.
Now customize the name of a clipboard to store your clips. 0000001811 00000 n Q:For the source coding: Hardware failures can also be attributed to design errors, inadequate or poor quality control during fabrication, overloading (use of under-capacity components) and wear out of mechanical parts. T or F, A:Question# Pigpen cipher is not susceptible to frequency analysis. We do not care whether the current page table is lost in a crash, since the system recovers by using the shadow page table. A:here, in line 1, square variable has been declared globally. Backpatching is the activity of filling unspecified information of labels. Activate your 30 day free trialto unlock unlimited reading.
See our User Agreement and Privacy Policy. In Floating Point Addition, the exponents of the two numbers being added need to be made equal before the mantissa fields can be added, as this ensures that the bit positional values are now aligned, Affine, Autokey and Keyed Transposition Ciphers. 0000005718 00000 n Q:are the advantages and disadvantages of the MUX and the decoder methods over conventional methods of, A:MUX: What are the advantages and disadvantages of the MUX and the decoder methods over one another? Discuss the advantages and disadvantages of paging. Each table entry points to a page on the disk. What are the disadvantages of shadow-paging? The cost of maintaining these requisites and manage a database system can be substantial. 2. false, Q:q .Pigpen cipher is not susceptible to frequency analysis. 0000016989 00000 n 1. It is a table that is in an array that is mainly used for, Q:How does the fingerprinting algorithm work?
A:Given question wants extended form of SHDSL. Clipping is a handy way to collect important slides you want to go back to later.
Q:List RC6 algorithm security with advantages and drawbacks, A:* RC6 is a symmetric key block cipher derived from RC5. Q:What is the difference between sampling and quantization? 1. true 2. false, A:Question. 1. true xref If you use 2 byte pixel values in a 24 bit lookup table representation, how many bytes does the look up table occupy? A:Given question wants expansion of jpg.
There are, however, disadvantages to the shadow-paging approach, as we shall see, that limit its use. It can use the trailer of the frame for error detection A:Given question is based on protocols in cs. 1. SlideShare uses cookies to improve functionality and performance, and to provide you with relevant advertising. It is important that the shadow page table be stored in nonvolatile storage, since it provides the only means of locating database pages. Shadow paging is one of the techniques that is used to recover from failure. the lookup, A:Definition: A:This short question is related to computer theory. Q:What is the value of J in SoP format? Q:Question: Show complete working of algorithm on training and receiver. Q:Mention the drawback of Mono alphabetic cipher. S.NANDHINI These statements are written in a simple English language. Free access to premium services like Tuneln, Mubi and more. Instead, when a page is to be modified, a shadow page is allocated. 0000016866 00000 n A:Decoding is theprocess of translating print into speech by rapidly matching a letter or combination, Q:Write the syntax for masking out all values greater than 0 in X, A:We use numpy masked_where function passing parameter the boolean condition to select all mask out, Q:Why Playfair Cipher is known as digraph cipher, A:Playfair cipher: 1)As given in the question is to provide the solution of the advantages APIdays Paris 2019 - Innovation @ scale, APIs as Digital Factories' New Machi Mammalian Brain Chemistry Explains Everything. and the, Q:What are the differences between Huffman coding and LZW coding? testing data for Speech Decoder? Q:What is the probability that a bit string of length 8 has exactly five 1s? O ne of the disadvantages of DBMS is database systems require sophisticated hardware, software, and highly skilled personnel. Q:Explain and discuss Cryptarithmetic Problem with a real example. Q:What are the difference between semaphores and mutexes? Pigpen cipher is a type of geometric substitution cipher. The first practical digraph i is playfair cipher. Allows multiple granularities of locking for the same object.
0000016802 00000 n 123 0 obj<>stream SlideShare uses cookies to improve functionality and performance, and to provide you with relevant advertising. Under what circumstances does shadow paging not require a log? *Response times may vary by subject and question complexity. It does not require the use of log in a single user environment. Find answers to questions asked by students like you. What are the advantages of Aries in DBMS? Shadow Paging maintains 2 page table. 0000015207 00000 n We all know that recovery means to get back the information, which is lost. <]>> After every transaction completion database pages containing old version of modified data need to be garbage collected. Page table is an index of pages. Looks like youve clipped this slide to already. Under certain circumstances, shadow paging may require fewer disk accesses than do the log-based methods discussed previously. For the source coding:What is/are the benefit(s) of calculating entropy? 0000017125 00000 n Activate your 30 day free trialto continue reading. Instant access to millions of ebooks, audiobooks, magazines, podcasts and more. P = C E (IV +n, K) 101 0 obj <> endobj The old copy of the database has not been affected. trailer 0 Affine cipher is not susceptible to frequency analysis. Send Flowers internationally on the Same Day, Solar System For Cannabis Indoor Farming House: Saving Your Bill, Best Affiliate Programs To Make Money In 2021. What are the advantages and disadvantages of the MUX and the decoder methods over one another? What are the differences between Huffman coding and LZW coding? xb```"wV| &{9-N. A:Solution:-- Shadow Database is an optional software facility available with Reality, whereby two copies of a database are maintained on the same system to enhance the resilience of the database in the event of a failure. 0000001737 00000 n Lookup table: A:In given question we have asked what is the probability that a bit string of length 8 has exactly, A:Backpatching It helps to maintain database consistency in case of failure. A:Given question is related to protocols in computer science. Initially we are provided with a string of characters known as plain text and a number know. Blockchain + AI + Crypto Economics Are We Creating a Code Tsunami? If you continue browsing the site, you agree to the use of cookies on this website. 0000009846 00000 n 0000001658 00000 n A:This question requires short form of given term. No change in the satisfaction ability of the Skolem standard form is achieved by the. It helps to maintain database consistency in case of failure.Advantages. What are the disadvantages of using the shadow-paging technique? See our Privacy Policy and User Agreement for details. What is/are the benefit(s) of calculating entropy? The compressed sparse row (CSR) or Yale format is a similar array, Q:Describe the key design ideas of Block cipher, A:The Feistel cypher structure is used in the construction of block cyphers. 0000011606 00000 n A:In artificial intelligence, the given message is encoded into a coded form; hence, it is not, Q:What is the relative efficiency of RCBD (Randomized Completely Block Design) over CRD (Completely, A:The relative efficiency of RCBD (Randomized Completely Block Design) over CRD (Completely Randomized, Q:If we use 12-bit pixel values in a lookup table representation, how many entries does Q:Affine cipher is not susceptible to frequency analysis. We use cookies to ensure that we give you the best experience on our website. Paging is a sort of memory storage that, Q:If you use 2-byte pixel values in a 24-bit lookup table representation, how many bytes does the, A:Definition: 0000000016 00000 n Aries supports page-level and record-level locking in a uniform fashion. False. A:Required:
* Block size of 128 bits Q:What is The Full form of VOIP in Computer Science? layer of OSI model can use the trailer of the frame for error detection. Median response time is 34 minutes for paid subscribers and may be longer for promotional offers. Learn faster and smarter from top experts, Download to take your learnings offline and on the go. For AES with a 128-bit block length and a 128-bit key length, what is the output, Q:Write the necessary steps for AES to do encryption and decryption with well-arranged diagrams for, A:According to the question we need to write the necessary steps for AES to do encryption and, A:Systematic error detection: A disadvantage of the general monoalphabetic cipher is that both sender and Q:3. startxref The advantages of paging must be determined. Structured English uses a simple English language to make structured programming easier for non-professionals.
Shadow paging is a copy-on-write technique for avoiding in-place updates of pages. For example, it is hard to extend shadow paging to allow multiple transactions to execute concurrently. We all know that recovery means to get back the information, which is lost. Give suitable reason for the solution, For AES with a 128 bit block length and a 128-bit key length, what is the output of the first round of AES if the plaintext consists of 128 1's and the first subkey also consists of 128 zeroes. A shadow database is a database that is built and used inside organizations, without IT knowledge or approval (hence the shadow in the title). The SlideShare family just got bigger. A:Answer 3 a) its named after lord playfair. BUFFER MANAGEMENT A:The answer for given question is option (C) Q# Pigpen cipher is not susceptible to frequency analysis.
So, the answer is, A MUX is a, Q:(True/False): Linking OBJ modules is much faster than assembling ASM source files, A:The time taken to assemble large source files will be more and because of it the code is being, A:Introduction:
0000001769 00000 n 0000001333 00000 n Does the Hamming code have a pattern? First of all, we have to understand what multiplexer is?? 16VE. Lookup table: 0000013375 00000 n In a computer operating system, paging is used for faster access of the data. The program is divided into various parts that are known as logical statements. Answer is in, A:Introduction of Paging: 0000003917 00000 n Therefore, data is transformed into, A:- The question wants to validate the statement that data is transferred into key-value pairs when, A:The question is on: The statement "MapReduce works on key-value pairs for input and output., Q:implements the Frame Check Sequence (FCS) using a technique called Cylic Redundancy Check (CRC).True, A:Required: We have to explain error detection mechanisms and framework of, Q:For CTR, on the lecture notes, it shows the decryption rule is Start your trial now! Q:What is The Compressed form of Multivariant Curve Resolution in Computers? %%EOF Which of the following are disadvantages of shadow paging? Q:Can someone explain to me what the trace back error means? True A:Answer is Data Link Layer The current page table may be kept in main memory (volatile storage). Enjoy access to millions of ebooks, audiobooks, magazines, and more from Scribd. Shadow paging is one of the techniques that is used to recover from failure. Flexible buffer management during restart and normal processing. Q:What is The Full form of XMPP in Computer Science? Q:What is The Full form of MIPS in Computer Science? 0000017207 00000 n The lookup table is mainly an array which will replace the. What are the disadvantages of shadow paging recovery technique? 0000016733 00000 n SHADOW PAGING AND Recovery not affected by granularity of locking. 3. OF ARTS & SCIENCE , NADAR SARASWATHI COLLEGE
 0000000756 00000 n
Describe its principle of operation, A:Fingerprints are made of an arrangement of ridges called friction ridges. However, a multiuser environment requires log for concurrency control. Q:What is the full form of VoIP in Computer Science? If you continue to use this site we will assume that you are happy with it. Due to location change on disk due to update database it is quite difficult to keep related pages in database closer on disk. %PDF-1.4
%
Python implementation. PRESENTED BY Disadvantages: Data gets fragmented or scattered. VADAPUDUPATTI , THENI.
0000000756 00000 n
Describe its principle of operation, A:Fingerprints are made of an arrangement of ridges called friction ridges. However, a multiuser environment requires log for concurrency control. Q:What is the full form of VoIP in Computer Science? If you continue to use this site we will assume that you are happy with it. Due to location change on disk due to update database it is quite difficult to keep related pages in database closer on disk. %PDF-1.4
%
Python implementation. PRESENTED BY Disadvantages: Data gets fragmented or scattered. VADAPUDUPATTI , THENI. A:What are the difference between semaphores and mutexes? Explain, True/False In computer science, shadow paging is a technique for providing atomicity and durability (two of the ACID properties) in database systems. During commit operation, changed blocks are going to be pointed by shadow page table which have to be returned to collection of free blocks otherwise they become accessible. T or F, A:Pigpen cipher: but, for the main function in the. Step 1 Page is a segment of memory. First week only $4.99. * Flexibility of, Q:For AES with a 128 bit block length and a 128-bit key length, what is the output of the first round, A:Given requirement, In each ridge, there are, A:Introduction: These databases are usually created by individual employees using Excel spreadsheets, notes on their desktop using Word, or Outlook contact, etc. 0000001416 00000 n This scheme is based on making copies of the database, called shadow copies, assumes that only one transaction is active at a time. Is Ea typo?, A:No, its not a typo as a many algorithm uses the E meaning encryption to decrypt the real meaning of. 0000017263 00000 n If you continue browsing the site, you agree to the use of cookies on this website. : How to Move Forward When We're Divided (About Basically Everything), Already Enough: A Path to Self-Acceptance, Full Out: Lessons in Life and Leadership from America's Favorite Coach, How to Be Perfect: The Correct Answer to Every Moral Question, Uninvited: Living Loved When You Feel Less Than, Left Out, and Lonely, Girl, Wash Your Face: Stop Believing the Lies About Who You Are so You Can Become Who You Were Meant to Be, Boundaries Updated and Expanded Edition: When to Say Yes, How to Say No To Take Control of Your Life, Never Split the Difference: Negotiating As If Your Life Depended On It, The 7 Habits of Highly Effective People Personal Workbook, Less Fret, More Faith: An 11-Week Action Plan to Overcome Anxiety, Girl, Stop Apologizing: A Shame-Free Plan for Embracing and Achieving Your Goals, The 7 Habits of Highly Effective People: Powerful Lessons in Personal Change: 25th Anniversary Infographics Edition, Anxious for Nothing: Finding Calm in a Chaotic World, Plays Well with Others: The Surprising Science Behind Why Everything You Know About Relationships is (Mostly) Wrong, Ahead of the Curve: Using Consumer Psychology to Meet Your Business Goals, Be the Love: Seven Ways to Unlock Your Heart and Manifest Happiness, Momentum: Setting Goals with Clarity, Intention, and Action, Do Hard Things: Why We Get Resilience Wrong and the Surprising Science of Real Toughness, How to Transform a Broken Heart: A Survival Guide for Breakups, Complicated Relationships, and Other Losses, Golden: The Power of Silence in a World of Noise, Stimulus Wreck: Rebuilding After a Financial Disaster, Endure: How to Work Hard, Outlast, and Keep Hammering, Courage and Crucibles: Leadership in Challenging Times, Speak: Find Your Voice, Trust Your Gut, and Get From Where You Are to Where You Want To Be, Life Lessons Harry Potter Taught Me: Discover the Magic of Friendship, Family, Courage, and Love in Your Life, The Expectation Effect: How Your Mindset Can Change Your World, The Mom Friend Guide to Everyday Safety and Security: Tips from the Practical One in Your Squad, Dad on Pills: Fatherhood and Mental Illness. A:In digital signal processing and related fields, sampling and quantization are two methods, rather. A`BC + AB`C` +AB, Data And Network Communication Technology. Systematic error detection is a technique where the error-checking, Q:Explain how to break a character substitution cipher, A:Answer: One copy is enabled as the live database to which users can log on. Specifically address the type of redundancy addressed by each method. Huffman encoding is an algorithm that encodes data in a lossless manner. In computer science, Algorithms for Recovery and Isolation Exploiting Semantics, or ARIES is a recovery algorithm designed to work with a no-force, steal database approach; it is used by IBM DB2, Microsoft SQL Server and many other database systems. A:Compressed sparse row: Q:MapReduce works on key-value pairs for input and output. Ethernet implements the Frame Check Sequence (FCS) using a technique called Cylic. Shadow Paging is a recovery technique that provides atomicity and durablity in database system.
Now customize the name of a clipboard to store your clips. 0000001811 00000 n Q:For the source coding: Hardware failures can also be attributed to design errors, inadequate or poor quality control during fabrication, overloading (use of under-capacity components) and wear out of mechanical parts. T or F, A:Question# Pigpen cipher is not susceptible to frequency analysis. We do not care whether the current page table is lost in a crash, since the system recovers by using the shadow page table. A:here, in line 1, square variable has been declared globally. Backpatching is the activity of filling unspecified information of labels. Activate your 30 day free trialto unlock unlimited reading.
See our User Agreement and Privacy Policy. In Floating Point Addition, the exponents of the two numbers being added need to be made equal before the mantissa fields can be added, as this ensures that the bit positional values are now aligned, Affine, Autokey and Keyed Transposition Ciphers. 0000005718 00000 n Q:are the advantages and disadvantages of the MUX and the decoder methods over conventional methods of, A:MUX: What are the advantages and disadvantages of the MUX and the decoder methods over one another? Discuss the advantages and disadvantages of paging. Each table entry points to a page on the disk. What are the disadvantages of shadow-paging? The cost of maintaining these requisites and manage a database system can be substantial. 2. false, Q:q .Pigpen cipher is not susceptible to frequency analysis. 0000016989 00000 n 1. It is a table that is in an array that is mainly used for, Q:How does the fingerprinting algorithm work?
A:Given question wants extended form of SHDSL. Clipping is a handy way to collect important slides you want to go back to later.
Q:List RC6 algorithm security with advantages and drawbacks, A:* RC6 is a symmetric key block cipher derived from RC5. Q:What is the difference between sampling and quantization? 1. true 2. false, A:Question. 1. true xref If you use 2 byte pixel values in a 24 bit lookup table representation, how many bytes does the look up table occupy? A:Given question wants expansion of jpg.
There are, however, disadvantages to the shadow-paging approach, as we shall see, that limit its use. It can use the trailer of the frame for error detection A:Given question is based on protocols in cs. 1. SlideShare uses cookies to improve functionality and performance, and to provide you with relevant advertising. It is important that the shadow page table be stored in nonvolatile storage, since it provides the only means of locating database pages. Shadow paging is one of the techniques that is used to recover from failure. the lookup, A:Definition: A:This short question is related to computer theory. Q:What is the value of J in SoP format? Q:Question: Show complete working of algorithm on training and receiver. Q:Mention the drawback of Mono alphabetic cipher. S.NANDHINI These statements are written in a simple English language. Free access to premium services like Tuneln, Mubi and more. Instead, when a page is to be modified, a shadow page is allocated. 0000016866 00000 n A:Decoding is theprocess of translating print into speech by rapidly matching a letter or combination, Q:Write the syntax for masking out all values greater than 0 in X, A:We use numpy masked_where function passing parameter the boolean condition to select all mask out, Q:Why Playfair Cipher is known as digraph cipher, A:Playfair cipher: 1)As given in the question is to provide the solution of the advantages APIdays Paris 2019 - Innovation @ scale, APIs as Digital Factories' New Machi Mammalian Brain Chemistry Explains Everything. and the, Q:What are the differences between Huffman coding and LZW coding? testing data for Speech Decoder? Q:What is the probability that a bit string of length 8 has exactly five 1s? O ne of the disadvantages of DBMS is database systems require sophisticated hardware, software, and highly skilled personnel. Q:Explain and discuss Cryptarithmetic Problem with a real example. Q:What are the difference between semaphores and mutexes? Pigpen cipher is a type of geometric substitution cipher. The first practical digraph i is playfair cipher. Allows multiple granularities of locking for the same object.